Unveiling the Security and Efficiency: The Schnorr Signature
In the rapidly evolving landscape of cryptography and blockchain technology, ensuring the security and efficiency of digital transactions remains a paramount concern. In this context, the Schnorr signature has emerged as a groundbreaking cryptographic scheme, offering enhanced security, scalability, and versatility. This article delves into the depths of the Schnorr signature, exploring its origins, inner workings, advantages, and its impact on various domains, particularly within the realm of blockchain and cryptocurrency.
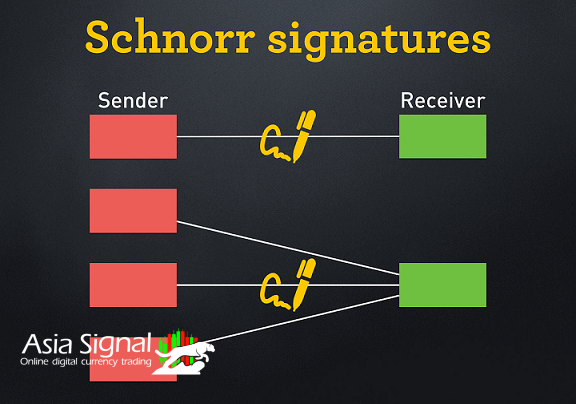
The Genesis of Schnorr Signature: A Historical Prelude
The story of the Schnorr signature begins with its visionary creator, Claus-Peter Schnorr, a German mathematician and cryptographer, who introduced the concept in 1989. Schnorr's signature scheme gained attention due to its elegant mathematical foundation and its potential to revolutionize digital signatures in terms of both security and efficiency.
Before the advent of the Schnorr signature, various signature schemes, such as the Digital Signature Algorithm (DSA) and the more well-known RSA (Rivest-Shamir-Adleman), dominated the cryptographic landscape. However, these schemes had their limitations, ranging from susceptibility to certain attacks to computational inefficiencies. The Schnorr signature, with its innovative approach, aimed to address these shortcomings and provide a more robust alternative.
The Mathematics Behind Schnorr Signature
At the core of the Schnorr signature lies its mathematical foundation, which is based on number theory and the discrete logarithm problem. To understand the essence of the Schnorr signature, one must delve into its mathematical intricacies.
The Schnorr signature process involves the following key components:
1. Key Generation: The signer generates a random private key, which is kept secret, and derives the corresponding public key using a one-way function.
2. Commitment: The signer commits to the message they wish to sign using a commitment function. This commitment is based on the private key and the message.
3. Challenge Generation: A challenge is generated by hashing the commitment and the public key. This challenge serves as a unique identifier for the signature process.
4. Response Calculation: The signer then calculates the response using the private key, the challenge, and other parameters.
5. Final Signature: The final signature is a combination of the response and the commitment.
The Schnorr signature's robustness relies on the difficulty of the discrete logarithm problem, which posits that finding the logarithm of a given number to a specified base is computationally infeasible. This mathematical foundation forms the bedrock of the scheme's security, making it resistant to attacks from adversaries attempting to forge signatures or reveal private keys.

Advantages of Schnorr Signature
The Schnorr signature brings forth a plethora of advantages that contribute to its increasing popularity in modern cryptography, particularly in blockchain applications.
1. Security:
The Schnorr signature excels in terms of security due to its reliance on the discrete logarithm problem. Unlike some older signature schemes, it is not susceptible to attacks such as the "ROCA" vulnerability that affected certain RSA implementations. This robustness makes it a dependable choice for applications that demand high levels of security.
2. Efficiency:
Efficiency is a crucial consideration, especially in resource-constrained environments like blockchain networks. The Schnorr signature boasts a compact signature size, which reduces the computational burden and minimizes the data storage requirements. This compactness results in faster verification times, a critical factor in blockchain systems aiming to achieve high transaction throughput.
3. Linearity:
A remarkable feature of the Schnorr signature is its linearity property. This property allows multiple signatures to be aggregated into a single signature, simplifying complex multi-signature scenarios. This capability aligns seamlessly with the scalability requirements of modern blockchain networks, where aggregating multiple transactions' signatures can significantly reduce the overall computational load.
4. Security Assumptions:
Schnorr signatures are designed to be secure under the well-established discrete logarithm problem assumption. This robust mathematical foundation ensures that even as computational capabilities evolve, the security of Schnorr signatures remains intact, providing long-term security guarantees.
5. Adaptive Security:
Schnorr signatures offer adaptive security, which means they remain secure even if an adversary gains partial knowledge of the private keys. This property enhances the scheme's resilience in scenarios where private keys might be partially compromised.
6. Improved Privacy:
The Schnorr signature's linearity property extends to multi-signature schemes, which can improve the privacy of participants in a multi-signature transaction. By aggregating signatures, observers are unable to discern the individual signers' identities, contributing to enhanced privacy.
Schnorr Signature in Blockchain and Cryptocurrency
The emergence of blockchain technology and cryptocurrencies catalyzed a reevaluation of cryptographic primitives, with a particular focus on improving security, scalability, and efficiency. Schnorr signatures found a natural home in this environment, and their adoption has sparked notable advancements in blockchain and cryptocurrency domains.
1. Bitcoin's Adoption:
Bitcoin, the pioneering cryptocurrency, recognized the potential of Schnorr signatures to enhance its protocol. The Bitcoin Improvement Proposal (BIP) 340 proposed the integration of Schnorr signatures into the Bitcoin network. This integration holds the promise of improving the network's scalability, reducing transaction fees, and enhancing privacy.
2. Scalability and Transaction Throughput:
Schnorr signatures' linearity property is a game-changer for blockchain scalability. In scenarios where multiple parties are involved, such as multi-signature wallets, the aggregation of signatures significantly reduces the computational load. This reduction translates into faster transaction verification times and a higher throughput for blockchain networks.
3. Lightning Network:
The Lightning Network, a second-layer solution built on top of blockchain networks like Bitcoin, aims to facilitate faster and cheaper transactions. Schnorr signatures play a crucial role in enhancing the Lightning Network's efficiency by enabling more complex and compact payment channel constructions.
4. Confidential Transactions:
Confidential transactions are a cryptographic technique employed to enhance the privacy of blockchain transactions. Schnorr signatures' compactness and linearity properties make them a perfect fit for confidential transactions, ensuring that transaction amounts and other sensitive information remain confidential while still being verifiable.
5. Interoperability and Standardization:
Schnorr signatures are not limited to a single blockchain. Their versatility and robustness have led to discussions about incorporating them into various blockchain platforms beyond Bitcoin, contributing to a standardized approach to digital signatures across different ecosystems.
Challenges and Future Prospects
While Schnorr signatures hold immense promise, no technology is without its challenges. The introduction of new cryptographic primitives necessitates careful analysis and scrutiny. Researchers and developers must thoroughly assess potential vulnerabilities, ensure proper implementation, and consider potential attacks that adversaries might employ.
As for the future, Schnorr signatures are likely to become a staple in cryptographic protocols, particularly in the realm of blockchain and cryptocurrency. The ongoing research and development surrounding Schnorr signatures will likely focus on optimizing their integration, standardization, and exploring innovative use cases that can harness their full potential.
Conclusion
The Schnorr signature stands as a testament to the continuous evolution of cryptography, demonstrating how a single innovative concept can reshape entire domains. With its strong mathematical foundation, efficiency, security, and versatility, Schnorr signatures have cemented their place in the toolkit of modern cryptographers and blockchain enthusiasts alike. As blockchain technology matures and the need for secure and scalable digital signatures grows, the impact of the Schnorr signature is set to reverberate across industries
Asiasignal, is The best Crypto VIP signals reference for you.

















Comments