The Fascinating World of Public Keys and Private Keys: Unveiling the Foundations of Digital Security
In the vast and intricate realm of modern digital communication and cryptography, the terms "public key" and "private key" stand as cornerstones of security and privacy. These concepts underpin the secure transmission of information, authentication, and encryption, allowing us to navigate the digital landscape with confidence. As we embark on a journey to unravel the complexities of public and private keys, we delve into their origins, mechanics, applications, and the crucial role they play in safeguarding our online interactions.

Origins and Fundamentals: Laying the Groundwork
The concept of public-key cryptography, which forms the basis for the public key and private key system, emerged in the early 1970s as a revolutionary idea. Prior to this breakthrough, encryption primarily relied on symmetric key systems, where a single key was used for both encryption and decryption. This posed a significant challenge: the secure exchange of a shared secret key between parties without compromising its confidentiality.
Whitfield Diffie and Martin Hellman, two pioneers in the field, published their seminal paper "New Directions in Cryptography" in 1976. This paper introduced the concept of asymmetric cryptography, where two mathematically related keys - the public key and the private key - could be used for encryption and decryption without the need for a shared secret key. This groundbreaking notion laid the foundation for modern secure communication.
The Mechanism: Public Key and Private Key Dynamics
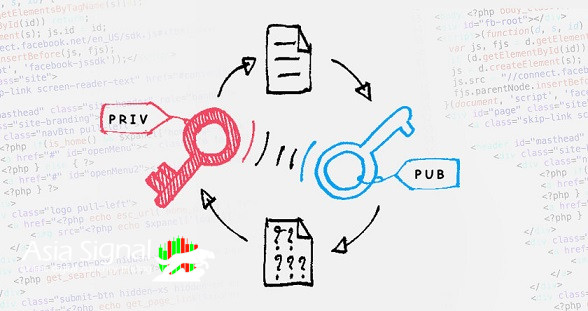
At the heart of the public key and private key system lies a mathematical relationship that enables the encryption and decryption of data. Each individual or entity is equipped with a pair of keys - a public key and a private key. These keys are mathematically related but are designed in such a way that it is computationally infeasible to derive the private key from the public key.
1. Public Key: As the name suggests, the public key is intended to be shared openly with anyone who wishes to communicate with the key holder. It is used to encrypt data that only the corresponding private key can decrypt. This property ensures the confidentiality of the information being transmitted. Remarkably, while anyone can use the public key to encrypt data, only the private key holder can decrypt it.
2. Private Key: The private key is a closely guarded secret, known only to the key holder. It is used for decrypting data that has been encrypted using the corresponding public key. Possession of the private key is essential for gaining access to encrypted information. As a result, the security of the private key is paramount in maintaining the integrity of the encrypted communication.
Applications and Use Cases: Enabling Secure Digital Interactions
The public key and private key system has far-reaching applications in various aspects of modern digital life:
1. Secure Communication: The system ensures secure communication between parties over insecure channels, such as the internet. When data is encrypted using the recipient's public key, only they can decrypt it with their private key.
2. Digital Signatures: Public key cryptography enables the creation of digital signatures, which serve as electronic equivalents of handwritten signatures. These signatures verify the authenticity and integrity of digital documents, assuring that they have not been tampered with during transmission.
3. Authentication: Public keys are also used in authentication protocols. When a user logs into a secure system, they can use their private key to prove their identity without transmitting sensitive information like passwords.
4. Secure E-commerce: Public keys play a vital role in securing online transactions. They facilitate the secure exchange of payment information and personal data, safeguarding sensitive details from unauthorized access.
5. Blockchain Technology: The security of blockchain networks, which underpin cryptocurrencies and decentralized applications, is reliant on public key cryptography. Wallet addresses and transactions are protected by the cryptographic keys.
Challenges and Future Directions: Navigating Complexity
While public key cryptography has revolutionized digital security, it's not without challenges:
1. Key Management: Safeguarding private keys is crucial. Loss or compromise of a private key can result in a breach of sensitive data or unauthorized access.
2. Quantum Computing: The advent of quantum computing poses a potential threat to classical encryption algorithms. Quantum computers could potentially break existing cryptographic methods, necessitating the development of quantum-resistant algorithms.
3. Trust and Authenticity:The system relies on a trust model where users must trust the authenticity of public keys. If an attacker can manipulate or impersonate key distribution, security can be compromised.
In Conclusion: Guardians of Digital Security
In the ever-evolving digital landscape, the concepts of public keys and private keys shine as guardians of our security and privacy. Their elegant mathematical foundations, versatile applications, and profound impact on secure communication make them indispensable tools in the modern age. As technology continues to advance and security threats evolve, the ongoing refinement of these cryptographic techniques will remain paramount in ensuring the confidentiality, integrity, and authenticity of our digital interactions.
We have provided you with the best foreign digital currencysignals , forex and futures signals in AsiaSignal.

















Comments